|
Since version 2.4, H-Sphere offers enhanced Qmail SMTP server configuration.
Most enhancements have been added to fight spam at the server level.
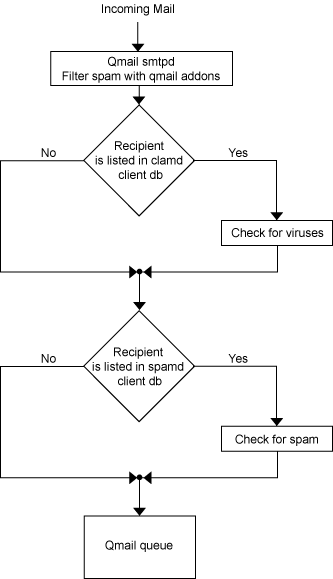
Antivirus and Antispam Filters (SpamAssassin and ClamAV)
Starting with H-Sphere 2.4, the Qmail update incorporates SpamAssassin and ClamAV filters at
the server level. It uses an improved qmail-queue patch concept, where the use of the QMAILQUEUE variable
is replaced with checking recipient addresses against the clamavclients and spamdclients
databases (see the drawing). H-Sphere users can add their mail addresses to the database to have them
checked for spam and viruses. User-defined antispam preferences are stored in a MySQL database.
Mail is filtered by standalone clamd and spamd services. We had to get rid of the Qmail-Scanner perl
wrapper, because it is rather heavy and unreliable for high load SMTP servers. Instead, we use
clamdmail software,
which is fast and adapted to working with clamd and/or spamd.
Updating Virus Patterns
Mail server cron has a script that updates virus patterns every day at 12AM.
You can manually change the timing of the cron.
Enabling Antivirus and Antispam
ClamAV and Spamassasin have been added to H-Sphere as resources,
and can be enabled and disabled from the control panel:
- Global Settings. In Info -> Global Resources, check
Antispam and Antivirus and click Submit Query.
- Plans. In Info -> Plans select the plans where
you would like to enable spam and virus protection. On the first page of the
wizard, enable Antispam and Antivirus. Optionally, set
prices for these resources on the subsequent steps.
Configuring ClamAV and SpamAssassin at the Server Level
Restarting ClamAV and SpamAssassin
See Restarting Services.
Updating ClamAV Database
Each hour cron updates ClamAV antivirus databases. Execute
crontab -l to see the list of cron tasks for a mail server.
The following line indicates that ClamAV database is updated each hour:
0 * * * * /hsphere/shared/bin/freshclam --quiet
ClamAV database update is configured in /hsphere/local/config/mail/clamav/freshclam.conf.
User Settings
ClamAV and Spamassasin settings can be configured per maildomain and
individual mailbox. Please see
User Guide for details.
Integrated Antispam Addons
Besides SpamAssassin, H-Sphere 2.4 Qmail includes a series of third party and in-house antispam addons.
This is the list for 2.4 Final:
- Fehcom Spamcontrol patch
(based on the spamcontrol-215 release) provided with opportunity
to switch whitelist extensions on and off dynamically;
- qmail-smtpd badmailfrom-unknown addon
- Qmail patch
to allow Qmail to use a concurrency greater than 240;
- doublebounce-trim patch
to discard doublebounces without queuing them;
- Jose Luis Painceira's patch that
deletes the body of bouncing messages.
This patch is based on Fred Lindberg's patch that
preserves the MIME-ness of bouncing MIME messages
- qmail-maildir++.patch (from Vpopmail distribution)
- Psoft addon that checks if the sender's address in POP-before-SMTP authentication is local
and the recipient's address is remote;
- Psoft addon that checks if domain name in the sender's address matches the domain name
used in SMTP authentication.
- Andre Oppermann's ext-todo patch,
which solves the 'silly qmail syndrome'. That's where qmail spends more time processing incoming email than
scheduling deliveries.
- big-DNS patch,
which fixes oversize DNS packet problem.
- Modified version of Qmail chkuser 0.6 patch that
checks if the vpopmail recipient is valid before accepting the message.
Qmail Server Settings
Default Qmail server settings, including antispam options, can be
configured in the admin control panel in the E.Manager/Mail Servers menu:
- Select Mail Servers from the E.Manager menu:
- Click the Action icon in the Mail Server Settings section:
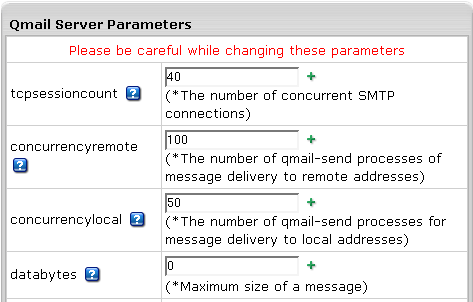
- Edit qmail settings following on-screen explanations and click Submit:
Important:
Values can be of three types:
- Text: can be either a line, like @12.34.56.78,
or a list, for example a list of addresses in badmailfrom.
badmailfrom is the file that containts a list of
senders mail isn't accepted from.
- Number, like 1000 in databytes.
databytes is the file that contains the maximum allowed size of
a message.
- Boolean, like 0 or 1 in smtpauth.
0 disables SMTP Auth, 1 enables it.
Note: 0 is also set by default if the corresponding control file is absent.
Thus, for example, if you have to enable SMTP Auth, you create/modify the
/var/qmail/control/smtpauth control file and put 1 in it. To disable SMTP Auth,
put 0 in the control file or just delete the control file.
Also, text values may contain patterns: wildcard expressions to set the range of
emails, domains and IPs for filtering rules.
Control characters in patterns:
- Exclamation mark (!): allows you to INCLUDE particular
clients/addresses by simply putting an exclamation mark (!) as first character in the line.
- Asterisk (*): General pattern matching character; one or more preceding.
- Question Mark (?): Match zero or one preceding.
- Backslash (\): Literal expression of following character, eg. \[.
- Match one from a set ([...]): i.e. [Ff][Aa][Kk][Ee] matches FAKE, fake, FaKe, FAKe etc.
- tcpsessioncount: the number of concurrent SMTP connections.
Default: 40. After setting this parameter,
Qmail restart is required.
- concurrencyremote: the number of qmail-send processes
of message delivery to remote addresses.
Default: 100. Max: 500. If Max is exceeded,
Max value is set.
- concurrencylocal: the number of qmail-send processes
for message delivery to local addresses.
Default: 50. Max: 500. If Max is exceeded, Max value is set.
- databytes: maximum size of a message.
Default: 0 (unlimited).
- queuelifetime: the message queue lifetime in seconds.
Default: 604800 (1 week).
- bouncefrom: the email user messages are bounced from.
Default: MAILER-DAEMON;
- maxrecepients: maximum number of recipients in the "TO:", "CC:", and "BCC" fields.
Default: 0 (unlimited).
- timeoutsmtpd: TCP connection timeout in seconds.
Default: 1200.
- newline: accept or reject mail from mail user agents (MUA)
that send commands without CR (carriage return).
Default: 0 (disabled);
- stripsinglequotes: enable or disable stripping single quotes (referred to in the
spamcontrol manual as the feature that may cause unpredictable results).
Default: 0 (disabled);
- lowercase: enable or disable conversion of mail address to lowercase; it may be useful in
filtering patterns, for case-sensitive rules.
Default: 0 (disabled).
- badmailfrom: list of sender addresses whose emails will be rejected. A line
in badmailfrom may be of the form @host, meaning every address at host.
Default: the badmailfrom file is absent (all sender addresses are allowed);
- badmailpatterns: the same as standard badmailfrom but with patterns. Example:
*@earthlink.net
!fred@earthlink.net
[0-9][0-9][0-9][0-9][0-9]@[0-9][0-9][0-9].com
answerme@save*
*%*;
Default: the badmailpatterns file is absent (all sender addresses are allowed);
- badmailfrom-unknown: if the domain part of sender's address matches a host in this list,
qmail checks if sender's IP has a PTR record.
Example
Default: the badmailfrom-unknown file is absent (reverse DNS check is disabled for all IPs);
- badhelo: filter HELO/EHLO sequence issued by SMTP client;
- badrcptto: list of recepient addresses for which all mail is blocked. A line
in badrecipient may be of the form @host, meaning every address at the host.
Default: the badrcptto file is absent (no recepient addresses are blocked);
- badrcptpatterns: the same as badrcptto but with patterns. It allows qmail-smtpd
to reject SPAM E-Mail including the signature
*\[dd.dd.dd.dd\]*
in the badrcptpatterns file, where dd.dd.dd is the IP address in brackets.
Default: the badrcptpatterns file is absent (no recepient addresses are blocked);
- blackholedsender: the same as badmailpatterns but quits the session immediately
even if quitasap is disabled;
- relayclients: list of IP addresses of clients allowed to relay mail through this host. Addresses
in relayclients may be wildcarded:
192.168.0.1:
192.168.1.:
Default: the relayclients file is absent (all client IPs are allowed to relay mail via this host);
- relaydomains: list of host and domain names allowed to relay mail through this host.
This is an additional mail relay check by the domain name, in case if
relay via the tcp.cdb static relay database is forbidden.
More on mail relays
Addresses in relaydomains may be wildcarded:
heaven.af.mil:
.heaven.af.mil:
Default: the relaydomains file is absent (all domains are allowed to relay mail);
- relaymailfrom: list of senders ("Mail From:") allowed to relay independently even if
open relay is closed. Entries in relaymailfrom can be E-Mail addresses, or just the domain (with the
@ sign). Unlike relaydomains, native addresses should be entered. Examples:
joeblow@domain1.com
@domain2.com
Default: the relaymailfrom file is absent (no senders are allowed to relay independently).
Important: For antispam security reasons, we strongly recommend not to add this parameter to
SMTP configuration.
- quitasap: enables (1) or disables (0) quitting SMTP session immediately
if one of the above rules works.
Default: 0 (no quitting);
- tarpitcount: the number of recepients after which qmail switches on
delay before sending the message to the next portion of recipients.
Default: 0 (no tarpitting);
- tarpitdelay: tarpitdelay is the time in seconds of delay to be
introduced after each subsequent RCPT TO:.
Default: 5.
- (in 2.4 beta 7) mfdnscheck:
enables (1) or disables (0) DNS check of domain name in sender's address. If enabled, no local domain check is performed.
Default: 0 (disabled);
- nomfdnscheck: list of domain names that aren't checked for existence. The list has the
same format as for relaymailfrom.
Default: the nomfdnscheck file is absent
(if mfdnscheck is enabled, all domains are checked for existence);
- helodnscheck: in a manner similar to mfdnscheck, performs check for HELO/EHLO smtp commands instead of
RCPT TO:.
- splithorizon: if 1, helodnscheck and badhelo checks for SMTP sessions with open
relay mfdnscheck are not performed.
- (2.4 beta 7+) userchk:
enables (1) or disables (0) check
that the vpopmail recipient is valid before accepting the message.
Default: 0 (disabled);
- smdcheck: allows only local domains in the MAIL FROM address if mail is sent remotely.
Default: 0 (any sender address is allowed);
- authsender: demands that domain name in the user address during SMTP authentication
should coincide with the domain name in the MAIL FROM address field.
Default: 0 (any sender address is allowed);
Default: 1 (POP-BEFORE-SMTP mode is on).
Important: To allow POP-BEFORE-SMTP, set this parameter to 1.
- rblhosts: RBL (Remote Black List) database hosts. Example:
dnsbl.njabl.org
spamguard.leadmon.net
Default: the rblhosts file is absent (RBL check is disabled: no external
RBL databases is being checked).
- (2.4.1+)
spamglobal: Antispam check of all incoming mail.
Default: 0 (disabled);
- (2.4.1+)
clamglobal: Antivirus check of all incoming mail
Default: 0 (disabled);
- (2.4.1+)
outgoingip: assign one of your network IPs for sending outgoing mail. If this value is not
empty, all your mail is sent from the specified IP, not from your actual mail server IP.
Use this control when your mail server IP is added to a spam blacklist, and mail from your domain
is rejected.
- periplimit: enter the number of simultaneous SMTP connections from the same IP.
- noathost: demands fully qualified domain email address in RCPT TO
and MAIL FROM smtp commands.
Default: 0 (disabled).
- ( in 2.4.3 Patch 1)
sanetcheck: enables/disables network check for SpamAssassin.
Default: 0 (disabled).
- ( in 2.4.3 Patch 1)
badurls: enables/disables sending any URLs contained in infected messages to the Comodo antispam database.
Default: 0 (disabled).
- urlscnt: specifies the number of "bad" URLs to be sent to the Comodo antispam database.
Default: 5
- ( in 2.4.3 Patch 1)
spamdchildren: specifies the number of forked spamd child processes.
Default: 10. We recommend to increase it for servers with large number of smtpd connections.
Note: As an example of patterns, see the canonical method filter for spam e-mail in
README_SPAMCONTROL
SPF (Sender Policy Framework)
(2.4.3 and up)
H-Sphere's SPF implementation at the SMTP server level is based on this
qmail patch.
It introduces the following qmail controls:
- spfbehavior: turns SPF checking on/off. The default value is 0 (off).
You can specify a value between 0 and 6:
- 0: Never do SPF lookups, don't create Received-SPF headers
- 1: Only create Received-SPF headers, never block
- 2: Use temporary errors when you have DNS lookup problems
- 3: Reject mails when SPF resolves to fail (deny)
- 4: Reject mails when SPF resolves to softfail
- 5: Reject mails when SPF resolves to neutral
- 6: Reject mails when SPF does not resolve to pass
Values bigger than 3 are strongly discouraged.
Important: This setting can be overridden using the
environment variable SPFBEHAVIOR, e.g. from tcpserver rules.
Note: If RELAYCLIENT is set, SPF checks won't run at all.
(This also includes SMTP-AUTH and similar patches)
-
spfrules: sets a line with local rules, i.e., rules that are executed before the real SPF rules
for a domain would fail (fail, softfail, neutral).
They are also executed for domains that don't publish SPF entries.
-
spfguess: sets a line with guess rules, i.e., rules that are used if the domain doesn't publish SPF rules.
The local spfrules are always executed afterwards.
-
spfexp: customized SPF explanation.
The explanation is the line returned to the SMTP sender when
a mail is rejected at the SMTP level. You can use macro expansion.
If a domain specifies its own explanation it is going to be used instead.
The SMTP answer when rejecting mails will look like:
550 the expanded SPF explanation (#5.7.1)
SRS (Sender Rewriting Scheme)
SRS is implemented with the following qmail control files located in the
/var/qmail/control/srs directory:
- revers_srs_secrets: contains keys called secrets to form hash for
SRS address for reverse mail. The file contains the list of secrets, each in separate line.
The most recent key is on top of the list. Qmail takes it first when checking SRS address,
and if it doesn't fit, Qmail takes these keys one after another. If none fit, the message will be rejected.
The file has 400 permissions and vpopmail:vchkpw ownership.
- srs_secrets: secrets for SRS address in forwards.
The file has 400 permissions and qmaill:qmail ownership.
- srs_secrets_age: an auxiliary file containing information when each key in
revers_srs_secrets and srs_secrets was created.
It is generated by the /var/qmail/bin/setsrssecret script and consists of the lines in the following format:
key timestamp
- srs_max_age: an integer value (in seconds) for the maximum permitted age of a rewritten address.
SRS rewritten addresses expire after a specified number of days
after which it is assumed no more bounces may be generated in response to the original mail. Mail sent to
expired SRS address is dropped without ceremony.
The default (about a month) should be appropriate for all purposes.
These controls are initiated and set by running the /var/qmail/bin/setsrssecret script.
You can run this script also as cron on mail servers.
Bounce Message Customization
H-Sphere 2.4.2 and higher enables bounce and doublebounce messaging in case if mail failed to be delivered.
Enter the necessary parameters and click Submit:
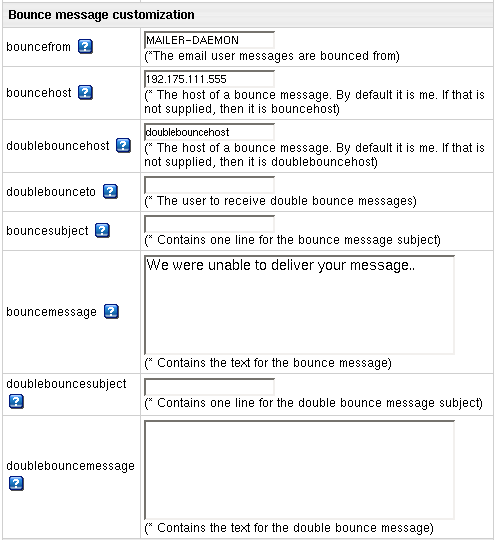
- bouncefrom: the email user messages are bounced from.
Default: MAILER-DAEMON;
- bouncehost: the host of a bounce message
Default: if not host IP, then it's bouncehost.
- doublebouncehost: the host of a doublebounce message
Default: if not host IP, then it's doublebouncehost.
- doublebounceto: the user email to receive doublebounce messages.
- bouncesubject: enter bounce message subject.
- bouncemessage: enter the text of the bounce message.
- doublebouncesubject: enter doublebounce message subject.
- doublebouncemessage: enter the text of the doublebounce message.
Mail Protocols
Choose a system SMTP relay for your mail server - POP before SMTP and SMTP AUTH.
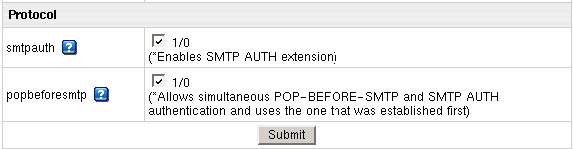
- smtpauth: enables SMTP AUTH extension.
Default: 0 (AUTH LOGIN/PLAIN/CRAM-MD5 SMTP extension is disabled);
- popbeforesmtp: allows simultaneous POP-BEFORE-SMTP and SMTP AUTH
authentication and uses the one that was established first.
Command Line Qmail Configuration
Qmail installation directory is usually /var/qmail/.
In H-Sphere before 2.4 patch 2, SMTPd configuration files are located in the /var/qmail/control directory.
They are also called control files. Each SMTP parameter is configured in its
own control file with the same name, for example, /var/qmail/control/smtpauth
for smtpauth parameter.
In H-Sphere 2.4 patch 2, all controls were gathered and placed in one configuration file,
/var/qmail/control/options.
To view SMTP server configuration, run the qmail-showctl utility, under root:
# /var/qmail/bin/qmail-showctl
You will get the list of SMTP parameters. Each line in the list has the following format:
smtp_parameter: [(Default.)] Value
Each stmp_parameter may be set in its own control file with the same name located in the
/var/qmail/control directory..
The file contains the parameter's value.
If the file is not found, the default value is taken and the default notification
(Default.) shows up in the configuration list.
|